Payment screening
Updated on 27.02.26
1 minute to read
Copy link
Overview
Screen payments in milliseconds against sanctions and watchlists to rapidly detect and prevent suspicious or illicit activity. SEON’s payment screening software adds a crucial layer of protection by screening both the sender and the receiver involved in a payment transaction against global screening lists in a single API call. This real-time check supports compliance with both international and regional sanctions, PEP, watchlist, criminal and adverse media sources, all before funds move. It also extends protection to check counterparty banks against sanction lists based on SWIFT/BIC codes or the names of financial institutions. It screens against sanctioned crypto wallets for broader coverage and faster detection.
- Real-time screening: Detect and act on risky payments in milliseconds.
- Single API integration: All screening happens within the Fraud API request.
- Comprehensive coverage: Screen both sender and receiver, whether individuals or companies, all in one request with no extra steps.
- Expanded identifiers: Check BIC and SWIFT codes against blocked and sanctioned institutions.
- Crypto wallet checks: Assess wallet addresses for links to high-risk or flagged entities
- Fine-tuned control: Customize matching logic using fuzzy, phonetic and score-based thresholds.
- Fully Integrated: Manage results via SEON’s Scoring Engine, Alerts and Case Management UI.
Payment Screening is an API-first solution that requires integration with the Fraud API. However, the results can also be managed through the Case management and Scoring Engine pages within SEON.
What's it for
- Payment processors, wallets, digital banks, remittance apps or others that need counterparty due diligence.
- Businesses in regulated sectors looking to cut manual work without compromising compliance.
- Companies seeking effective risk mitigation without introducing downstream friction or exposing the business to compliance penalties.
Key concepts
| Term | Description |
| Sender | The party initiating a transaction |
| Receiver | The party receiving a transaction |
| Payment screening | AML customer screening using configurable sources and logic |
| AML sources | Global sanctions lists, PEPs, watchlists, crime cists, adverse media, sanctioned SWIFT/BIC codes, sanctioned crypto wallets |
| Fuzzy matching | Includes edit distance, phonetic match and configurable score thresholds |
API integration
Enabling payment screening
Include a payment_screening object within the AML section of your Fraud API V2 request configuration. This object contains two configuration blocks:
sender_configreceiver_config
Each block allows you to define separate risk settings for the sender and receiver in a transaction.
Additional bank screening configuration
To enable bank screening and receive bank-related details in the response:
- Include a new
aml_bank_screeningobject in your configuration. - Enable
aml_bank_screening_api. - Add
aml_bank_screening_detailsto the config.response_fields string, alongsideaml_details. - Add bank details:
receiver_bank_name,receiver_bank_account,receiver_bank_swift
This ensures that both payment and bank screening details are returned in the Fraud API response.
Example request
{
"config":{
"aml_bank_screening":{
"bank_name_check":true,
"bank_account_check":true,
"bank_swift_check":true
},
"aml":{
"payment_screening":{
"sender_config":{
"type":"UNKNOWN",
"sources":{
"sanction_enabled":true,
"pep_enabled":true,
"watchlist_enabled":true,
"crimelist_enabled":true,
"adversemedia_enabled":true
},
"fuzzy_enabled":true,
"fuzzy_config":{
"phonetic_search_enabled":false,
"edit_distance_enabled":true,
"scoring":{
"result_limit":10,
"score_threshold":0.585,
"adverse_media_scores":{
"fuzziness":0,
"exact_match":true,
"force_dob_filter":true,
"force_country_filter":true
}
}
}
},
"receiver_config":{
"type":"UNKNOWN",
"sources":{
"sanction_enabled":true,
"pep_enabled":true,
"watchlist_enabled":true,
"crimelist_enabled":true,
"adversemedia_enabled":true
},
"fuzzy_enabled":true,
"fuzzy_config":{
"phonetic_search_enabled":false,
"edit_distance_enabled":true,
"scoring":{
"result_limit":10,
"score_threshold":0.585,
"adverse_media_scores":{
"fuzziness":0,
"exact_match":true,
"force_dob_filter":true,
"force_country_filter":true
}
}
}
}
}
},
"aml_api":true,
"aml_bank_screening_api":true,
"response_fields":"aml_details,aml_bank_screening_details"
},
"user_fullname":"Example Name",
"user_firstname":"Example",
"user_middlename":"",
"user_lastname":"Name",
"user_dob":"1990-01-01",
"user_pob":"Budapest",
"user_photoid_number":"56789",
"user_id":"123456",
"receiver_fullname":"string",
"receiver_firstname":"string",
"receiver_middlename":"string",
"receiver_lastname":"string",
"receiver_dob":"1980-01-01",
"receiver_pob":"string",
"receiver_photoid_number":"string",
"receiver_id":"string",
"receiver_country":"string",
"user_bank_name":"User Bank",
"user_bank_account":"User Bank Account",
"user_bank_swift":"User Bank SWIFT",
"user_bank_country":"country code",
"receiver_bank_name":"Receiver Bank",
"receiver_bank_account":"Receiver Bank Account",
"receiver_bank_swift":"Receiver Bank SWIFT"
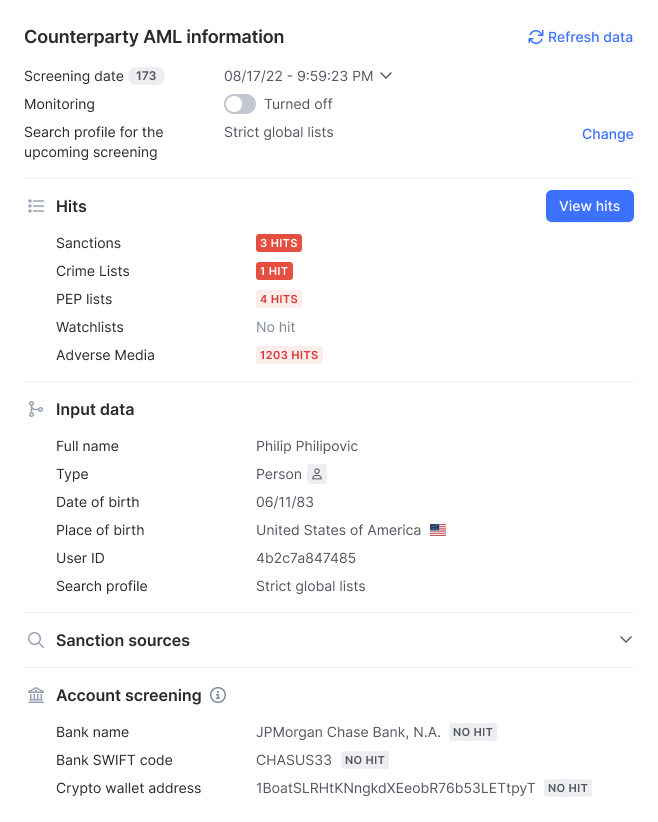
}Once a bank screening is requested, all related bank account screening information, such as the bank name, SWIFT code and crypto wallet address will appear in the AML information or Counterparty AML information widget, allowing you to review these details alongside other screening results.
Customizing risk profiles
You can configure different fuzzy matching and data source preferences for both the sender and receiver. This flexibility allows compliance officers to tailor the risk screening strategy for each party in a transaction.
For instance, SEON customers may choose to apply a more thorough screening, such as enabling PEP and watchlist checks, for their own users, while applying a more targeted check (e.g., sanctions only) for the counterparty, depending on the associated risk level and desired objectives.
Learn more about the configuration options available in this integration guide.
Input validation for payment screening
To ensure the Payment Screening process runs correctly, please be aware of the following input validation rules:
- If a
payment_screeningobject is included with asender_configbut no receiver_config, only the sender will be screened. - If both
sender_configandreceiver_configare present anduser_fullnameis provided, butreceiver_fullnameis missing, only the sender will be screened
How to set up payment screening rules and alerts in SEON
Once a sender or receiver match is detected, you can utilize SEON’s Scoring Engine to take immediate action or surface alerts for further review:
- Automate actions with the Scoring Engine : Create compare rules in the Scoring Engine based on counterparty screening results. This enables automated decision-making, for example, you can automatically decline a transaction if the counterparty appears on a sanctions list or place the payment on hold pending further verification.
- Generate alerts in case management: Configure alerts to trigger when a screening match occurs. You can then review, annotate and escalate cases as needed using SEON’s case management tools all while keeping a complete audit history.
Use cases
Payment (outbound transaction)
In cases where funds are paid by a user, the beneficiary (the recipient of the transaction) should be added to the receiver_config. The nature of the transaction can be captured using the action_type field.
"config":
{
"aml_bank_screening": {
"bank_name_check": true,
"bank_account_check": true,
"bank_swift_check": true
}
"aml":{
"payment_screening": {
"sender_config": {
"type": "UNKNOWN",
"sources": {
"sanction_enabled": true,
"pep_enabled": true,
"watchlist_enabled": true,
"crimelist_enabled": true,
"adversemedia_enabled": true
},
"fuzzy_enabled": true,
"fuzzy_config": {
"phonetic_search_enabled": false,
"edit_distance_enabled": true,
"scoring": {
"result_limit": 10,
"score_threshold": 0.585,
"adverse_media_scores": {
"fuzziness": 0,
"exact_match": true,
"force_dob_filter": true,
"force_country_filter": true
}
}
}
},
"receiver_config": {
"type": "UNKNOWN",
"sources": {
"sanction_enabled": true,
"pep_enabled": true,
"watchlist_enabled": true,
"crimelist_enabled": true,
"adversemedia_enabled": true
},
"fuzzy_enabled": true,
"fuzzy_config": {
"phonetic_search_enabled": false,
"edit_distance_enabled": true,
"scoring": {
"result_limit": 10,
"score_threshold": 0.585,
"adverse_media_scores": {
"fuzziness": 0,
"exact_match": true,
"force_dob_filter": true,
"force_country_filter": true
}
}
}
}
},
"aml_api": true,
"aml_bank_screening_api": true,
"response_fields": "aml_details,aml_bank_screening_details"
},
"action_type": "outbound",
"user_fullname": "Example Name",
"user_firstname": "Example",
"user_lastname": "Name",
"user_dob": "1990-01-01",
"user_pob": "Budapest",
"user_photoid_number": "56789",
"user_id": "123456",
"receiver_fullname": "John Doe",
"receiver_firstname": "John",
"receiver_lastname": "Doe",
"receiver_dob": "1980-01-01",
"receiver_pob": "New York",
"receiver_photoid_number": "123456789",
"receiver_id": "987654",
"receiver_country": "US"
"user_bank_name": "User Bank",
"user_bank_account": "User Bank Account",
"user_bank_swift": "User Bank SWIFT",
"user_bank_country": "country code",
"receiver_bank_name": "Receiver Bank",
"receiver_bank_account": "Receiver Bank Account",
"receiver_bank_swift": "Receiver Bank SWIFT"
}
}
Bank transfer (inbound transaction)
In an inbound transaction, where the user is the beneficiary, the counterparty (payer) should be added to the receiver_config. The action_type should reflect the direction of funds, e.g., "action_type": "inbound".
"action_type": "inbound",
"user_fullname": "Example Name",
"user_firstname": "Example",
"user_lastname": "Name",
"user_dob": "1990-01-01",
"user_pob": "Budapest",
"user_photoid_number": "56789",
"user_id": "123456",
"receiver_fullname": "John Doe",
"receiver_firstname": "John",
"receiver_lastname": "Doe",
"receiver_dob": "1980-01-01",
"receiver_pob": "New York",
"receiver_photoid_number": "123456789",
"receiver_id": "987654",
"receiver_country": "US"
Purpose tagging (custom field)
In scenarios where transaction purpose matters (e.g., securities purchase), it can be specified in the custom_fields object.
"custom_fields": {
"transaction_purpose": "securities_purchasing_order"
}Adding custom metadata like this allows for enhanced auditability, monitoring and compliance reporting based on transaction context.
Input validation for payment screening
To ensure the payment screening process runs correctly, please be aware of the following input validation rules:
- If a
payment_screeningobject is included with asender_configbut noreceiver_config, only the sender will be screened. - If the
payment_screeningobject includes areceiver_configbut nosender_config, payment screening will be skipped entirely. - If both
sender_configandreceiver_configare present, anduser_fullnameis provided, butreceiver_fullnameis missing, only the sender will be screened. - If the
payment_screeningobject is present butuser_fullnameis not provided, payment screening will be ignored.