Default rules
Updated on 21.01.26
7 minutes to read
Copy link
Overview
To help you get started from day one, SEON contains a collection of default rules. These rules are divided into rule categories based on the data points they examine or the use case they're intended for. Find a description of each rule below.
While you can't edit the parameters of default rules you can change how they affect a transactions fraud score and turn them on or off. If you'd like to tweak one of these rules, duplicate it as a custom rule. By selecting multiple default rules, you can also batch turn on/turn off them off or copy them to custom rules.
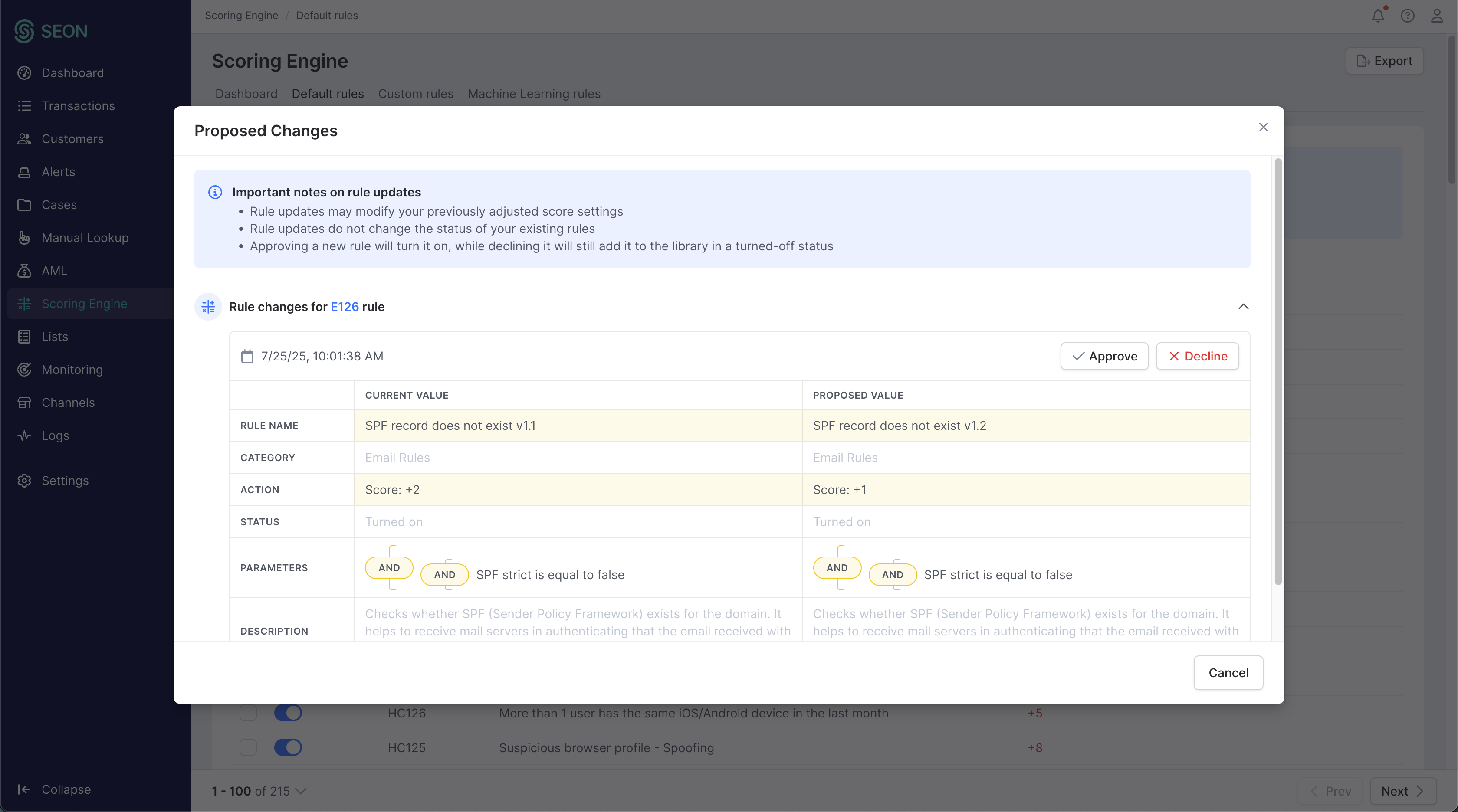
Default rule updates
To ensure our default rules remain effective, we continuously monitor and assess them to keep pace with evolving fraud trends and the specific needs of different verticals. When necessary, we propose updates to enhance protection.
These proposed changes will appear in your account, where you can review and choose to accept or decline them if you have the required permission. Although we recommend accepting the proposals, if they are not reviewed or are declined, the previous version will continue to function.
Email rules
A collection of rules designed to spot and flag suspicious email addresses. These rules focus on the digital history, format and domain of an email address to block fraudsters with newly minted or throwaway addresses.
Rule ID | Rule name | Description | Score |
| E100 | Domain is disposable | Checks whether the domain is listed as disposable. Messages received are deleted automatically in several days and many of them do not even require a password. | 80 |
| E101 | Email API result is unknown | In case the Email API could not run and return data, this rule will trigger. It can be used to spot these very rare cases. | 6 |
| E102 | Domain is custom and was registered less than 1 month ago. No online profiles were found. It was not involved in a data breach | Checks whether the domain is custom, if it was registered in the last month, has no online profiles and if it has not been involved in a data breach. | 10 |
| E103 | Domain is custom and was registered between 1 and 2 months. No online profiles were found. It was not involved in a data breach | Checks whether the domain is custom, if it was registered in the last 1 to 2 months, has no online profiles and if it has not been involved in a data breach. | 8 |
| E104 | Domain is custom and was registered between 2 and 3 months. No online profiles were found. It was not involved in a data breach | Checks whether the domain is custom, if it was registered in the last 2 to 3 months, has no online profiles and if it has not been involved in a data breach. | 6 |
| E105 | Domain is custom and was registered more than 3 months ago. No online profiles were found. It was not involved in a data breach | Checks whether the domain is custom, if it was registered more than 3 months ago, has no online profiles and if it has not been involved in a data breach. | 4 |
| E106 | Domain is custom and was registered less than 1 month ago. No online profiles were found. It was involved in at least a data breach | Checks whether the domain is custom, if it was registered in the last month, has no online profiles and if it has been involved in at least 1 data breach. | 2 |
| E107 | Domain is custom and was registered less than 2 months ago. At least 1 online profile was found. It was not involved in a data breach | Checks whether the domain is custom, if it was registered in the last 2 months, has at least 1 online profiles and if it has not been involved in a data breach. | 2 |
| E108 | Domain is custom and was registered more than 2 months ago. At least 1 online profile was found. It was not involved in a data breach | Checks whether the domain is custom, if it was registered more than 1 month ago, has at least 1 online profiles and if it has not been involved in a data breach. | 0 |
| E109 | E109 Domain is custom and was registered more than 1 month ago. At least 1 online profile was found. It was involved in at least a data breach. | Checks whether the domain is custom, if it was registered more than 2 months ago, has at least 1 online profiles and if it has not been involved in a data breach. | 0 |
| E110 | Domain is custom and was registered more than 1 month ago. No online profiles were found. It was involved in at least a data breach | Checks whether the domain is custom, if it was registered more than 1 month ago, has no online profiles and if it has not been involved in a data breach. | 2 |
| E111 | Domain is a free provider. The only online platform found is identical to the provider. It was not involved in a data breach | Check whether the domain is a free provider i.e.: gmail.com, yahoo.com, etc., number of tied online profiles and if the email was involved in a data breach. | 8 |
| E112 | Domain is a free provider. The only online platform found is identical to the provider. It was involved in at least a data breach | Check whether the domain is a free provider i.e.: gmail.com, yahoo.com, etc., number of tied online profiles and if the email was involved in a data breach. | 4 |
| E113 | Domain is a free provider. At least 2 online profiles were found. It was involved in at least a data breach | Check whether the domain is a free provider i.e.: gmail.com, yahoo.com, etc., number of tied online profiles and if the email was involved in a data breach. | 0 |
| E114 | Domain is a free provider. No online profiles were found. It was not involved in a data breach | Check whether the domain is a free provider i.e.: gmail.com, yahoo.com, etc., number of tied online profiles and if the email was involved in a data breach. | 10 |
| E115 | Domain is a free provider. At least 2 online profiles were found. It was not involved in a data breach | Check whether the domain is a free provider i.e.: gmail.com, yahoo.com, etc., number of tied online profiles and if the email was involved in a data breach. | 1 |
| E116 | Domain is a free provider. 1 online profile was found. It was involved in at least a data breach | Check whether the domain is a free provider i.e.: gmail.com, yahoo.com, etc., number of tied online profiles and if the email was involved in a data breach. | 2 |
| E117 | Domain is a free provider. 1 online profile was found. It was not involved in a data breach | Check whether the domain is a free provider i.e.: gmail.com, yahoo.com, etc., number of tied online profiles and if the email was involved in a data breach. | 4 |
| E118 | Domain is a free provider. No online profiles were found. It was involved in at least a data breach | Check whether the domain is a free provider i.e.: gmail.com, yahoo.com, etc., number of tied online profiles and if the email was involved in a data breach. | 3 |
| E119 | Domain is high risk | Checks whether the domain associated with the email is listed on our internal high-risk domain list. | 7 |
| E120 | Domain is not registered | Checks whether the domain has an ‘owner’ or can be purchased. | 20 |
| E121 | Email is not deliverable | Checks whether the email can receive messages. For this we use SMTP-MX checks to see whether the email is deliverable. | 8 |
| E122 | 5 or more digits in email handle or in username | Checks whether there are 5 or more numerical values in the customers email handle or username. | 1 |
| E123 | Email is not similar to user full name | Check whether the email address is similar to the user's full name. | 0 |
| E124 | Mail server is configured to accept all | Checks whether the mail server is set up to "accept all" emails. "accept-all" is a domain-wide setting mail server that is configured to accept all emails sent to the domain, no matter if the specified mailbox exists or not. | 1 |
| E125 | Mail server's DMARC is not enforced | DMARC (Domain-based Message Authentication, Reporting, and Conformance) provides domain owners the ability to enforce a DMARC policy, which will 1 cause the email to be rejected on the receiver side if it fails authentication. | 1 |
| E126 | SPF record does not exist | Checks whether SPF (Sender Policy Framework) exists for the domain. It helps to receive mail servers in authenticating that the email received with a given domain is truly sent from the domain server. | 1 |
| E127 | Suspicious TLD | Checks whether the top-level domain of the domain name is considered suspicious. The top-level domain is the last part of the domain name (eg. in the case of seon.io, the TLD is ‘io’). | 1 |
| E128 | Website does not exist on email's domain | Checks whether there is a website present for the domain. | 0 |
| E129 | Domain’s registrar name is high risk | Checks if the domain registrars (company that manages internet domain names) are considered suspicious because of the domains they manage (eg. Netowl Inc.). | 5 |
| E130 | Customer is using Private Email Relay Service | Checks if a user has private relay email service used, private relay email service sends email to a recipient using an automatically generated email address (eg. domain: privaterelay.appleid.com) | 2 |
| E131 | Suspicious email format | Checks whether the email doesn’t contain vocals or numbers and are not privaterelay.email users, i.e., automatically generated email addresses for Apple users | 0 |
| E132 | ‘Hide my email pattern’ match | Compares pattern of email provider with the typical pattern of emails created with Apple's 'Hide My Email' feature, used for hiding original email from spam/unwanted emails. This feature is often abused during any onboarding process to create multiple accounts. | 2 |
| E133 | Possible domain typo | Looks for possible typos in the email domain. We've compiled a list of domain typos to scan. In most cases, these email addresses are not valid, but most likely due to an unintentional error. | 0 |
IP rules
This collection of default rules considered the technical characteristics of a customer's internet connection and IP address. Identify suspicious settings and flagged IP addreses with ease.
Rule ID | Rule name | Description | Score |
| P100 | There is 1 suspicious open port on the IP address | An open port exposes the services that are listening to it (waiting for data) for potential exploits. | 4 |
| P101 | There are 2 or more suspicious open ports on the IP address | An open port exposes the services that are listening to it (waiting for data) for potential exploits. | 8 |
| P102 | Port 80 is open on the IP address | Port 80 is the most common port hackers use to gain access to devices. | 1 |
| P103 | Customer is using TOR | TOR (The Onion Router) is a free browser, which hides the Internet traffic from network surveillance or traffic analysis by utilizing its overlay network. | 95 |
| P105 | Customer is using a Web proxy | Web proxy is similar to a public proxy, with the difference that a web proxy may be dedicated to only one user, while the same public proxy could be used by multiple users at the same time. | 20 |
| P106 | Customer is using a datacenter ISP | Datacenter ISP means that the user is connecting from a server ISP, not a residential ISP (like Vodafone, or T-Mobile). Many Nordic users use VPN solutions, and VPN users are most probably presented as DCH users. All VPN users are DCH, but not all DCH are VPNs. A datacenter also works as a middleman between the destination and the user desktop. | 10 |
| P107 | IP address was found on 1 spam blacklist | We check whether the IP address is listed on any of 70+ spam lists. | 0 |
| P108 | IP address was found on 2 spam blacklists blacklist. | We check whether the IP address is listed on any two of 70+ spam lists. | 2 |
| P109 | IP address was found on 3 spam blacklists | We check whether the IP address is listed on any 3 of 70+ spam lists. | 3 |
| P110 | IP address was found on 4 spam blacklists | We check whether the IP address is listed on any 4 of 70+ spam lists. | 4 |
| P111 | IP address was found on 5 spam blacklists | We check whether the IP address is listed on any 5 of 70+ spam lists. | 5 |
| P112 | Customer is using a public proxy | Proxy servers are the middlemen between end-users and the destination that they browse. Both the end-users and the destination website communicate with the proxy server, not directly with each other. | 10 |
| P113 | Customer is using a remote access protocol | Checks if the necessary ports for remote access are open at the user’s IP address. | 1 |
| P114 | Customer is using a harmful IP address | Check if the IP address is harmful, i.e. was it involved in large scale ATO attacks or similar behavior | 2 |
Phone rules
Similar to email addresses, people use their phone numbers online a lot. These rules consider the digital breadcrumbs left by that usage and technical characteristics to identify risk.
Rule ID | Rule name | Description | Score |
| PH100 | At least 2 online profiles were found | Checks if at least 2 online profiles are connected to the user's phone number. | 0 |
| PH101 | At least 1 online profile was found | Checks if at least 1 online profile is connected to the user's phone number. | 1 |
| PH102 | No online profile was found | Checks if 0 online profiles are connected to the user's phone number. | 4 |
| PH103 | Phone is not valid nor possible | Checks whether the syntax, format, length, and prefix is correct for the given phone number. | 10 |
| PH104 | Phone is suspicious | Check if the phone number is suspicious | 3 |
| PH105 | Phone is disposable | Checks if the phone is disposable | 10 |
Device Rules
With Device Fingerprinting up and running in your account, you will gain access to the following rules that will help you identify suspicious device behavior, connections, and configurations.
Rule ID | Rule name | Description | Score |
| HC100 | Timezone based on IP geolocation and user's device does not match | Checks whether the device timezone and the IP location timezone matches. | 2 |
| HC101 | There are more than 2 different IP addresses detected using WebRTC | WebRTC (Web Real-Time Communication) allows web browsers to set up a direct connection with the destination website. It makes it possible to exchange live audio and video online without having to use any additional software. As a result, it can expose the true IP address of the device, even if the user connects with a VPN for example. | 2 |
| HC102 | Cookies are not enabled on user's side | Checks whether cookies are enabled in the user’s browser. | 2 |
| HC106 | Missing device details | Missing device details. | 0 |
| HC108 | Customer's mobile device is an emulator | Checks whether the device is an emulator. An emulator simulates or mimics the hardware and software of mobile devices on a desktop without actually having a physical mobile device. | 8 |
HC109 | Customer's mobile device is jailbroken | Checks whether the device is jailbroken. It is mostly performed on iOS devices. Jailbreaking removes the restrictions Apple puts in place, allowing the user to install third-party software from outside the app store. Applicable for SDK integration. | 4 |
HC110 | Customer's mobile device is rooted | Checks whether the device is rooted. Rooting gives the ability to alter or replace system applications and settings, run specialized applications that require administrator-level permissions or perform other operations that are otherwise inaccessible. Applicable for SDK integration only and rooting is generally performed on Android devices. | 5 |
HC113 | Unpopular device screen resolution | Identifies devices with unusual screen resolutions, which may be indicative of suspicious activities. | 2 |
HC114 | Unpopular user agent | Detects browsers that are uncommon based on their user agent string, which may be indicative of suspicious activities. | 2 |
HC115 | Suspicious browser profile – Potential fraud browser | Detects browsers frequently associated with fraudulent activities. | 5 |
HC116 | Suspicious browser profile – Privacy browser | Identifies browsers that have built-in anti-fingerprinting features, typically used to enhance user privacy. | 1 |
HC117 | Suspicious browser profile – Bots and automation | Detects browsers that are likely automated (controlled by software rather than a human), indicating potential bots and automated scripts. | 12 |
HC118 | Suspicious browser profile – Privacy extension | Detects privacy extensions possibly modifying the browser's fingerprint. | 2 |
HC119 | Suspicious browser profile – Low risk | Evaluates the browser profile for signs of low-risk device signals activities based on device information. | 1 |
HC120 | Suspicious browser profile – Medium risk | Evaluates the browser profile for signs of medium-risk device signals based on device information. | 3 |
HC121 | Suspicious browser profile – High risk | Evaluates the browser profile for suspicious device signals, including Virtual Machine detection. | 5 |
HC122 | Browser version age is between 1–2 years | This rule detects when a browser has not been updated to the latest versions within 1 to 2 years. | 1 |
HC123 | Browser version age is between 2–5 years | Flags browsers that are 2 to 5 years out of date. This detection helps identify browsers that lack recent updates and may pose security risks. | 3 |
HC124 | Browser version age is greater or equal to 5 years | Flags browsers that have not been updated for more than 5 years. Such outdated browsers are unusual and may significantly increase security vulnerabilities. | 8 |
HC125 | Suspicious browser profile – Spoofing | Flags instances where a user manipulates their browser to appear as if they are using a different configuration, typically to evade detection. | 8 |
HC126 | More than 1 user has the same IOS/Android device in the last week | Checks if the same iOS/Android device has been used by more than 1 user in the last week. | 5 |
HC133 | Suspicious browser profile – Dynamic Component Blocked | The Dynamic Component is the module responsible for advanced checks of suspicious browser profiles. The blocking of this module may point to malicious activities. | 0 |
HC134 | Customer is using Proxy/VPN | Detects the usage of proxy services or VPNs by analyzing device signals. This method can identify even residential proxies. Utilizes browser fingerprinting via the JavaScript Agent for enhanced detection. | 0 |
HC135 | Click automator is installed | Identifies the presence of click automators, which may indicate bot activities or automated actions on the device. This rule is specifically implemented within the Android SDK. | 0 |
HC136 | Screen is mirrored to an additional display | Checks if the device's screen is being mirrored to an external display. This could indicate that the device's content is being viewed by others. This detection is specific to the Android SDK. | 0 |
HC137 | Remote desktop software is used | Determines if the device is currently being controlled by a recognized remote control application. This feature is specific to the Android SDK and helps identify unauthorized access. | 0 |
HC138 | Phone’s screen is captured during the transaction | Detects active screen recording, mirroring, or content streaming via AirPlay. This rule is specifically designed for the iOS SDK. | 0 |
HC139 | User is in a phone call during the transaction | Detects if the device is in an active call, including calls that are on hold. This rule covers calls made through GSM, VoIP, or a combination of both and is applicable to the Android and iOS SDKs. | 0 |
HC140 | Connected to PC via USB / USB Debugging enabled | Identifies if the device is connected to an Android Debug Bridge (ADB) debugger, which may represent a significant security risk. This detection is specific to the Android SDK. | 0 |
Other rules
A collection of rules to identify uncommon or suspicious setups or strange card usage patterns.
Rule ID | Rule name | Description | Score |
HC107 | Customer is from Nordic country and using VPN | Checks if the customer is from a Nordic country and is using a VPN | 10 |
HC111 | IP country is different from card country (card not prepaid or virtual) | Checks whether the card issuer country is different from the IP country. | 1 |
HC112 | Card country is a high HDI country but the IP country is a low HDI country or suspicious | Checks if the card from a high HDI (Human Development Index) country was used from a low HDI 2 IP country. | 2 |
HC127 | Customer's full name contains numbers | Checks if the customers full name contain numbers | 2 |
HC128 | Phone country and User country do not match | Checks if the user's phone country does not match the user's country | 2 |
HC129 | Phone country and IP country do not match | Check if the user's phone country does not match the user's IP country | 2 |
HC131 | Card is virtual or prepaid | Check if the user’s card is virtual or prepaid card | 0 |
HC132 | Card is corporate or business | Check if the user’s card is either corporate or business | 0 |
Login monitoring – Use case specific rules
These rules can help you catch fraudsters when they try to login to your services and thus support you in the fight against account takeover attacks.
Rule ID | Rule name | Description | Score | Requirements |
|---|---|---|---|---|
UC100 | 2 different IP countries within an hour | Alerts when there is at least two IP countries connected to login actions under the same User ID in an hour | 10 | IP country Action type User ID |
UC101 | Changing the password to the same as under 2 different accounts | Checks if there were password change actions for 2 different User IDs where the password hash is the same. | 4 | User ID Password hash Action type |
UC102 | HC117 was triggered on previous transaction for the same browser hash and IP address within 1 week | HC117 was triggered on previous transaction for the same browser hash and IP address within 1 week. Note: Rule HC117 checks datapoints collected by our Device Fingerprinting module that indicate automation was used during the transaction. | 10 | Applied rule ID HC117 Transaction ID Browser hash IP address |
UC103 | HC117 was triggered on previous transaction for the same IP address within 24 hours | HC117 was triggered on previous events for the same IP address within 24 hours. Note: Rule HC117 checks datapoints collected by our Device Fingerprinting module that indicate automation was used during the transaction. | 10 | Applied rule ID HC117 Transaction ID IP address |
UC105 | More than 1 actions except login fail have the same cookie hash in the last day with different full names and zip codes | More than one action other than login fail have the same cookie hash with different full names and zip codes within the last day. | 4 | Action type Transaction ID Cookie hash User full name User ID User zip |
UC106 | More than 2 logins from different countries within 1 day | Alerts when there were two different login actions from the same User ID with different IP locations | 10 | IP country Action type User ID |
UC107 | More than 5 failed account logins within 1 minute | The rule triggers if there are at least five failed login attempts with the same User ID, IP address and Device hash | 20 | Action type Transaction ID User ID Device hash |
UC108 | New device and password change for current transaction | Alerts when the Password hash count for the same User ID is at least two and there were no login action connected to the same User ID in the last month | 10 | Transaction ID User ID Action type Device hash Password hash |
UC109 | User country is different from IP country (no VPN) | The rule compares the user country against the IP country. | 8 | User country IP country VPN IP API |
UC110 | User has more than 2 browser hashes within 24 hours | Alerts when there are more than two browser hashes connected to the same User ID in a day | 2 | Browser hash User ID |
UC111 | User has more than 2 cookie hashes within 24 hours | Alerts when there are more than two cookie hashes connected to the same User ID in a day | 2 | Cookie hash User ID |
UC112 | User has more than 2 device hashes and IP addresses within 24 hours | Alerts when there are more than two IP addresses and more than two device hashes connected to the same User ID in a day | 5 | Device hash User ID IP address |
UC113 | User has more than 3 unique IP ISP names within the last hour | The rule searches for the third login attempt from the same User ID where the Internet Service Provider is different from the two previous ones and all the three attempts happened in an hour. | 8 | Action type User ID ISP name IP API |
UC114 | User never used a DCH and this device before | Alerts when there were previous transactions for the same User ID where the Internet Service Provider type is datacenter and the device hash is the same Note: P106 - Triggers if the Internet Service Provider is a datacenter | 10 | Applied rule IDP106 Transaction Id User ID Device hash |
UC115 | User never used spoofing, now login from spoofed device | There were no historical events for the same User ID, where the HC125 rule triggered, but for the current event the suspicious browser profile contains spoofing. Note: HC125 rule looks for data points collected by our Device Fingerprinting module that indicate the user is trying to mask their real device. | 5 | Applied rule HC125 User ID Transaction ID Suspicious browser profile |
Merchant monitoring – Use case specific rules
Designed for our partners in ecommerce, couple these rules with those in the Payment rules category to improve the protection of your online store. Catch suspicious orders or merchants before they damage your business
Rule ID | Rule name | Description | Score | Requirements |
|---|---|---|---|---|
UC116 | Amount is increased to 10000% compared to the previous transaction | Amount compared to the previous transaction has increased 10000%. | 10 | Transaction amount in EUR Action type Merchant ID |
UC117 | Card used with different addresses | Alerts when the Card hash was connected to other events but with different User address hash. | 3 | User address hash Card hash Merchant ID |
UC118 | Card used with multiple names | Alerts when the Card hash was connected to other events but with different Cardholder full name. | 5 | Cardholder full name Card hash Merchant ID |
UC119 | Cross-border card usage | Alerts when the number of IP countries for the same card hash and merchant ID is at least two in the last day. | 5 | IP Country Card hash Merchant ID |
UC121 | Same BIN used repeatedly with the same merchant | Alerts when there were at least five events with the same Merchant ID and Card BIN. | 5 | Transaction ID Merchant ID Card BIN |
UC123 | Transaction amount is greater than the 200% average transaction value (ATV) of all ecommerce/crypto/gambling operators | The rule compares the current transaction amount in EUR with previous transaction amounts in EUR connected to the same Merchant category. | 4 | Transaction amount in EUR Merchant category |
Payment monitoring – Use case specific rules
Avoid fraudulent payments, friendly and family fraud with SEON's purpose-built default rules. Blocking suspicious payments can reduce chargeback rates and helps you avoid the cost of handling fraudulent orders in general.
Rule ID | Rule name | Description | Score | Requirements |
|---|---|---|---|---|
UC124 | Billing country does not equal shipping country | 4 | Billing country Shipping country | |
UC125 | Card bleeding (decreasing amounts to test available funds on card) | 6 | Transaction ID User ID Action type | |
UC126 | Card country is not equal to IP country | 6 | BIN API IP API | |
UC127 | Card limit seeking | Alerts when a user is raising the spent amounts in order to reach the card limit | 8 | Fraud API
|
UC128 | Cardholder full name is not similar to user full name/Skype name/LinkedIn name, etc. | 2 | Cardholder full name Skype name Linkedin name Line name | |
UC129 | Cardholder name is not similar to User fullname | 10 | Cardholder full name User full name BIN API | |
UC130 | Current transaction 300% higher than in the last 3 months | 6 | User ID | |
UC131 | Deposit with new card is 500% larger than avg deposits so far | Alterts when the deposit is 5 times larger than the average with a new card | 10 | Action type Card hash Transaction amount |
UC132 | FTD is large (5k) | Alerts when the amount of the First Time Deposit is exceeding the given limit. | 5 | User created Action type Transaction ID User ID |
UC133 | High difference between deposit amounts (10000% with amounts 2-20 EUR, 1000% 20-200 EUR) | Alerts when the deposit amount is 100 or 10 times higher than the minimal the client usually deposits. Note: The amount is an example and subject to change depending on industry and client needs | 0 | Transaction Amount Action type |
UC134 | High difference between withdrawal amounts (10000% with amounts 2-20 EUR, 1000% 20-200 EUR) | Alerts when the withdrawal amount is 100 or 10 times higher than the minimal the client usually withdraws. Note: The amount is an example and subject to change depending on industry and client needs | 0 | Transaction Amount Action type |
UC135 | Item category falls into a greater price category | Alerts when the purchased item has a larger value. Note: This rule specific to eCommerce companies where they can use item category for their goods and can mark high value ones | 2 | Item fields |
UC136 | Medium difference between deposit amounts (5000% with amounts 2-20 EUR, 500% with amounts 20-200 EUR) | Alerts when the deposit amount is 50 or 5 times higher than the minimal the client usually deposits. Note: The amount is an example and subject to change depending on industry and client needs. | 0 | Transaction Amount Action type |
UC137 | Medium difference between withdrawal amounts (5000% with amounts 2-20 EUR, 500% with amounts 20-200 EUR) | Alerts when the withdrawal amount is 50 or 5 times higher than the minimal the client usually withdraws. Note: The amount is an example and subject to change depending on industry and client needs | 0 | Transaction Amount Action type |
UC138 | More than 1 user has the same card hash | 5 | User ID Card hash | |
UC139 | More than 10 purchases in the last 10 mins | 8 | Action type Transaction ID User ID | |
UC140 | More than 2 currencies are used for withdrawing funds in the last week by the same user | 1 | Action type Transaction currency User ID | |
UC141 | More than 2 unique card hashes in the last 24 hours | 8 | Card hash User ID BIN API | |
UC142 | More than 2 users have the same billing/shipping address | 2 | User ID Billing address hash Shipping address hash | |
UC143 | More than 3 card countries for the same user | Alerts when a user has More than 3 different card countries within a year. Note: The amount of card countries and the timeframe is customizable. | 6 | BIN BIN API |
UC144 | More than 5 CVV results in the last 1 minute | 10 | CVV result Card hash BIN API | |
UC145 | More than 5 purchases in the last 10 mins | 4 | Action type Transaction type User ID | |
UC146 | More than 5 transactions from the same IP address in the last 1 minute | 20 | Transaction ID IP address IP API | |
UC147 | More than 5 withdrawals in the last 1 day from the same user | 20 | Action type Transaction ID User ID | |
UC148 | No bets between deposits | Alerts when there was no bet made between two deposits | 4 | Action type |
UC150 | PayPal overpayment fraud | Alerts when the Transaction amount is higher than the item price with PayPal. Note: This is a classic scheme, where they request a refund on the overpaid amount from the merchant, then chargeback the rest via PayPal | 8 | |
UC151 | PayPal shipping address scams | Alerts when there are more users with the same shipping address using PayPal | 8 | Payment mode Shipping address |
UC152 | PayPal transfer as gift | Alerts when the item is bought as a gift | 2 | Gift Payment mode |
UC153 | Same card, different expiry date per minute | 5 | Card hash | |
UC154 | The current withdrawal amount is higher than the sum of the last 3 withdrawals | 4 | Action type User ID Transaction amount in EUR | |
UC155 | The current withdrawal is more than double of the average withdrawal amount | 6 | Action type User ID Transaction amount in EUR | |
UC156 | The sum of withdrawal amount in the last week is higher than the sum of withdrawal amount in the last month starting from the beginning of last week | Alerts when the withdrawal amount is is larger than the sum of all withdrawals in the 3 weeks before the current week. | 4 | Action type Transaction amount |
UC157 | The user has continuous activity in the last 3 months (at least 1 transaction each week) | 0 | Transaction ID User ID | |
UC158 | The user uses two cards multiple times alternatively in a short period of time | 8 | Card hash User ID Transaction ID | |
UC159 | There was chargeback with card, now user is coming with a card not used before | Note: Label API is a crucial to mark historical transactions in order to make it easier to follow up on fraudulent activities | 20 | Payment mode Transaction label User ID Transaction ID Card hash BIN API Label API |
UC160 | User deposits with 2nd card from a different country (not prepaid) within 1 day | 10 | Card country User ID BIN API | |
UC161 | User deposits with 3rd card from a different country (not prepaid) within 1 week | 5 | Card country User ID BIN API | |
UC162 | Withdrawal from a new country and new device vs. deposit from other | 6 | Action type Transaction ID Device hash User ID IP country Email API Device Fingerprinting | |
UC163 | Withdrawal value is over 15K EUR | The rule checks the withdrawal events, where the transaction amount in EUR is greater or equal to 15k | 2 | Action type Transaction amount in EUR |
UC164 | Withdrawal value is over 30K EUR | The rule checks the withdrawal events, where the transaction amount in EUR is greater or equal to 15k | 4 | Action type Transaction amount in EUR |
Registration monitoring – Use case specific rules
It's best to stem the flow of fraud at its source. Block fraudsters and bots from registering fake accounts for multi-accounting, abusing bonuses, or placing fraudulent orders.
Rule ID | Rule name | Description | Score | Requirements |
|---|---|---|---|---|
UC165 | Account created in private mode | Private/incognito mode was used during registration. Note: Using the private/incognito mode to register is usually not a genuine user behavior, and it might indicate fraudulent acivity | 3 | JS agent |
UC166 | Auto-generated session_id (suspicious_browser_profile contains auto_generated_session_id) | Checking the browser session for automated signs. Note: Session ID will be auto-generated to make sure there is one for JS agent. With good integration this rule will only trigger on suspicious transactions | 2 | JS agent |
UC167 | Cardholder name is not equal to User fullname | 5 | Cardholder full name User full name | |
UC168 | CNAM and LinkedIn names are not similar | 4 | CNAM Email address Email API | |
UC169 | Count of dots in email is equal or greater than 4 | Note: High amount of dots in an email address is usually sign of fraudulent activity | 2 | Email address Email API |
UC170 | Count of numbers and vowels equal to 0, email length greater than 4 | 5 | Email address Email API | |
UC171 | Device used with a different, blacklisted email address | Alerts when the device was previously used with a fraud email address Note: The rule will check events coming through web applications | 20 | Email address Email API JS agent |
UC172 | Device used with a different, blacklisted email address (native version) | Alerts when the device was previously used with a fraud email address Note: The rule will only check events where the native SDK is involved. | 20 | Email address Email API Android SDK iOS SDK |
UC173 | IP address was marked as fraud previously within the last 1 week | 10 | IP address IP API | |
UC174 | IP/email/browser hash is flagged | Alerts when either the IP address, email address or browser hash is flagged as fraudulent by another SEON user. | 10 | IP address IP API Email address Email API JS agent |
UC175 | IT social profile exists (Email) | Note: The email address is registered on on all IT related social platform. | 0 | Email address Email API |
UC177 | Linkedin connection count greater than 100 (or any number) | There are more than 100 LinkedIn connection for the email address. | -5 | Email address Email API |
UC178 | More than 1 user from the same brand/affiliate/merchant ID and IP address within an hour | Alerts when there are more than 1 one user coming from the same IP address and merchant, affiliate or brand ID. | 8 | IP address IP API Merchant ID Affiliate ID Brand ID |
UC179 | More than 1 user from the same browser hash within 1 hour | 5 | JS agent | |
UC180 | More than 1 user from the same password hash and IP address within 24 hours | 5 | Password hash IP address IP API | |
UC181 | Multiple registrations made with the same phone number | The rule checks registration events where at least two User IDs connected to the same phone number | 8 | Action type User ID Phone |
UC182 | Multiple registrations with the same cookie hash | The rule checks registration events where at least two User IDs connected to the same cookie hash | 5 | Action type User ID Cookie hash |
UC183 | Multiple registrations with the same device hash (Native app) | The rule checks registration events where at least two User IDs connected to the same sessions | 5 | User ID Action type Device hash Session source |
UC184 | Multiple registrations with the same Device ID | The rule checks registration events where at least two User IDs connected to the same Device ID | 5 | Action type User ID Device ID |
UC185 | Multiple registrations with the same IP address and Device hash | The rule checks registration events where at least two User IDs connected to the same device and IP address | 5 | Action type User ID IP address Device hash |
UC186 | Multiple registrations with the same user address hash | The rule checks registration events where at least two User IDs connected to the same user address hash | 6 | Action type User ID User address hash User street User zip User city |
UC187 | Multiple registrations with the same user fullname and ZIP | The rule checks registration events where at least two User IDs connected to the same User full name and User zip | 5 | Action type User ID User fullname User zip |
UC188 | Previous email similarity is high for the same email domain and browser hash within 1 week | Alerts when a highly similar email address was used previously from the same email domain and browser hash | 5 | Email address Email API JS agent |
UC189 | Russian social profile exists (Email) | 2 | Email address Email API | |
UC190 | Russian social profile exists (Phone) | 2 | Phone number Phone API | |
UC191 | Same email address used for suspicious registration under different brand | Alert when the email address was previously used on a different brand and it was a fraudulent transaction | 10 | Email address Email API Brand ID |
UC192 | Similar emails used with the same device | Alerts when email addresses from the same device are highly similar | 2 | Email address Email API Custom field: Referrer |
UC193 | Similar emails with the same Brand ID | Alerts when email addresses from the same Brand ID are highly similar | 2 | Email address Email API Brand ID |
UC194 | Similar user full names under the same Brand ID | Alerts when user full name from the same Brand ID are highly similar | 2 | User full name BrandID |
UC195 | Similar usernames under the same Brand ID | Alerts when the usernames from the same Brand ID are highly similar | 2 | Username BrandID |
UC196 | Similar usernames used with the same device | Alerts when the usernames from the same device hash are highly similar | 2 | Username JS Agent |
UC197 | Skype country is not equal to User country | 2 | User country Phone number Phone API Email address Email API | |
UC198 | Skype country not equal to Phone country | 8 | Phone number Phone API | |
UC199 | Average of fraud score for the same email address on different brand is greater than 20 | Alerts when transactions related to the email address on other have an average score of 20 or above | 20 | Email address Email API |
UC201 | User full name not similar to Skype/LinkedIn/Line name | 6 | User full name Email address Email API Phone number Phone API | |
UC202 | Zalo (Phone) profile for non-VN phone number | Note: Zalo is rarely used outside of Vietnam | 2 | Phone number |