Handling and resolving alerts
Updated on 04.12.24
4 minutes to read
Copy link
Overview
SEON’s alert system is designed to streamline investigations, ensure fair workload distribution, and maintain thorough documentation. By automating and structuring the alert-handling process, SEON enables your fraud and AML teams to work collaboratively and focus on the most critical tasks. This comprehensive approach makes investigations seamless and efficient, so your team can stay ahead of potential threats.
Assigning alerts
When a new alert is generated, SEON’s system ensures efficient task distribution by automatically assigning it to the team member subscribed to the relevant alert trigger. This auto-assignment prioritizes team members with the fewest pending tasks, balancing workloads and minimizing bottlenecks.
Auto-assignment in action: Alerts are seamlessly routed to the right team members, ensuring that no alert is left unattended. This automation allows your team to focus on resolving issues instead of manually delegating tasks.
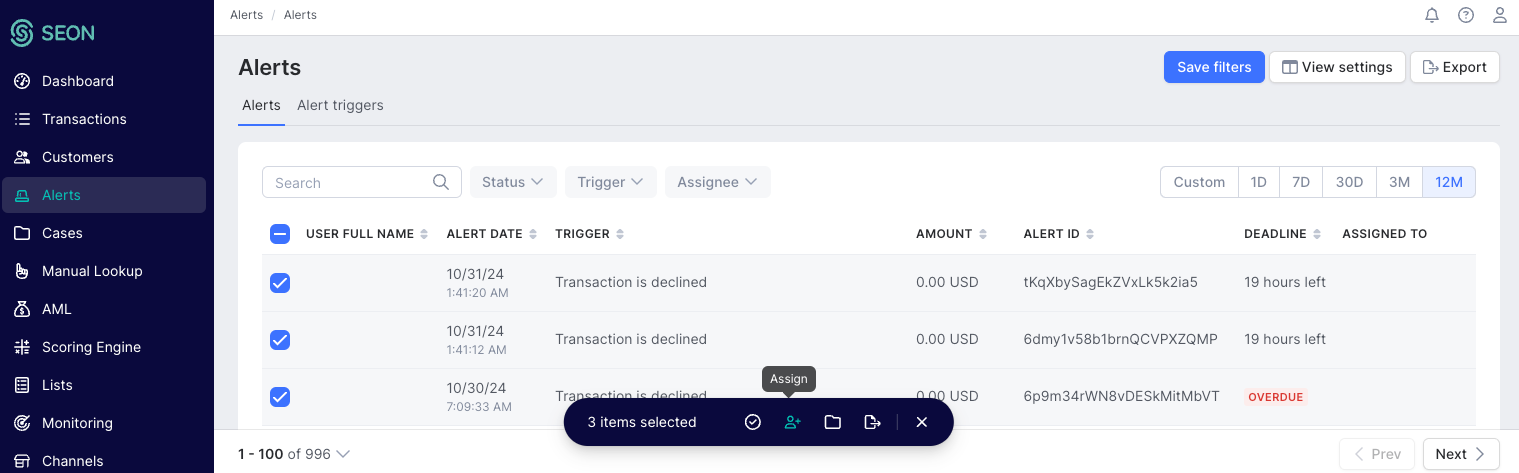
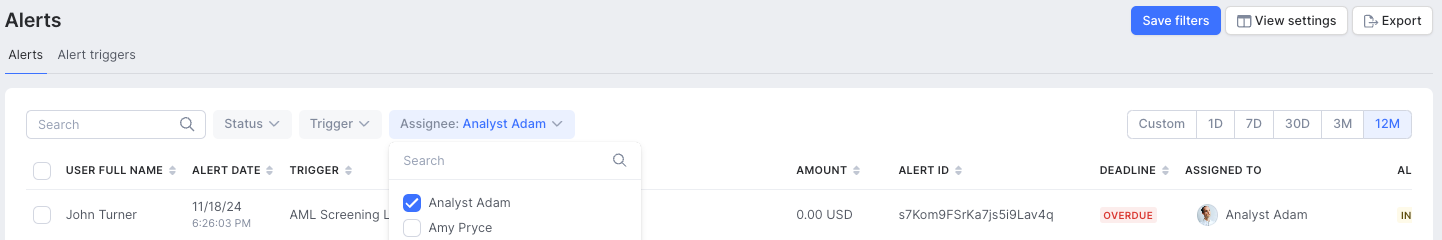
Manual assignment option: If needed, alerts can also be manually reassigned:
- Select one or more alerts from the Alerts page.
- Click the Assign button at the bottom of the screen.
- Choose the team member you want to delegate the alert to.
Once an alert is assigned to an AML analyst, their role is to assess whether the alert indicates a genuine AML threat requiring escalation, if it has a simple explanation, or if it’s a false positive.
Reviewing alerts
The Alert details page consolidates all relevant information into an intuitive, tabbed format. Each tab organizes data into sections for streamlined access and review, making investigations faster and more efficient.
Getting started: Summary tab
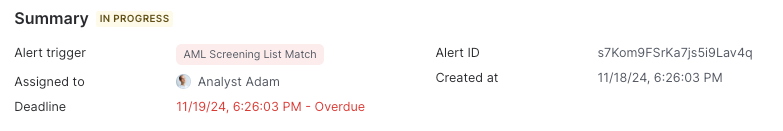
Most analysts begin their investigations in the Summary tab, which provides a clear overview of the alert, much like the layout of Transaction details.
Key details in this tab include:
- Alert trigger: What triggered the alert
- Assignment: Which team member is assigned to the alert
- Deadline and Created date: Key time markers for tracking urgency
You’ll also find transaction details, such as:
- Customer information: Full name, user ID and AML hits.
- Activity metrics: Fraud score, transaction amount, state and more.
In addition, SEON automatically aggregates related alerts and cases for the same customer, helping analysts quickly access connected investigations and gain a complete picture of potential risks.
Resolve alerts more efficiently with fraud and AML insights in one place
SEON goes beyond standard alert details by offering comprehensive insights into fraud and AML activity all in one place to empower data-driven decisions.
Insights include:
- Fraud score: A risk assessment based on SEON's Scoring Engine
- Blackbox score: A deeper dive into flagged behaviors
- Applied rules: Details of the rules that triggered the alert
- SEON data signals: Key information such as email, phone and device & OS data that SEON retrieved throughout the customer journey
Centralized documentation & notes for streamlined collaboration
SEON’s Documents and Notes widgets help your team maintain a clear, organized record of each investigation by centralizing evidence and observations in one place.
- Document uploads: Analysts can attach relevant materials directly within the Documents widget, keeping all evidence centralized and accessible throughout the investigation.
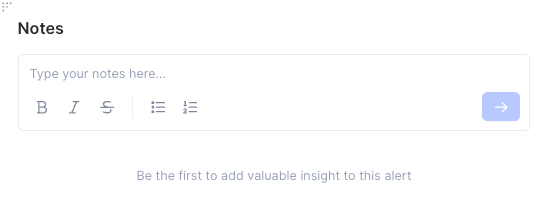
- Adding notes: Analysts can document findings in the Notes section, ensuring insights and key decisions are recorded. If the alert is escalated to a case, all notes remain visible to ensure continuity throughout the investigation lifecycle.
Uncover hidden patterns in the Customer Connections tab
The Customer Connections tab helps analysts identify relationships between users, devices and data points, providing critical context for investigations.
Key capabilities include:
- Connection insights: View all linked users associated with specific data points (e.g., IP, phone number, or address).
- Data categories: Investigate connections through fields such as IP address, phone number, billing and shipping addresses, device hash, email address
- Customizable timeframes: Analyze connections over time (e.g., last 30 days) to spot trends and potential fraud networks.
Use this tab to uncover hidden associations, such as multiple accounts created using the same device or shared IP addresses across unrelated users.
Dive deeper with the Raw data tab
The Raw data tab offers a detailed view of the request payload associated with the alert, providing technical information for API requests.
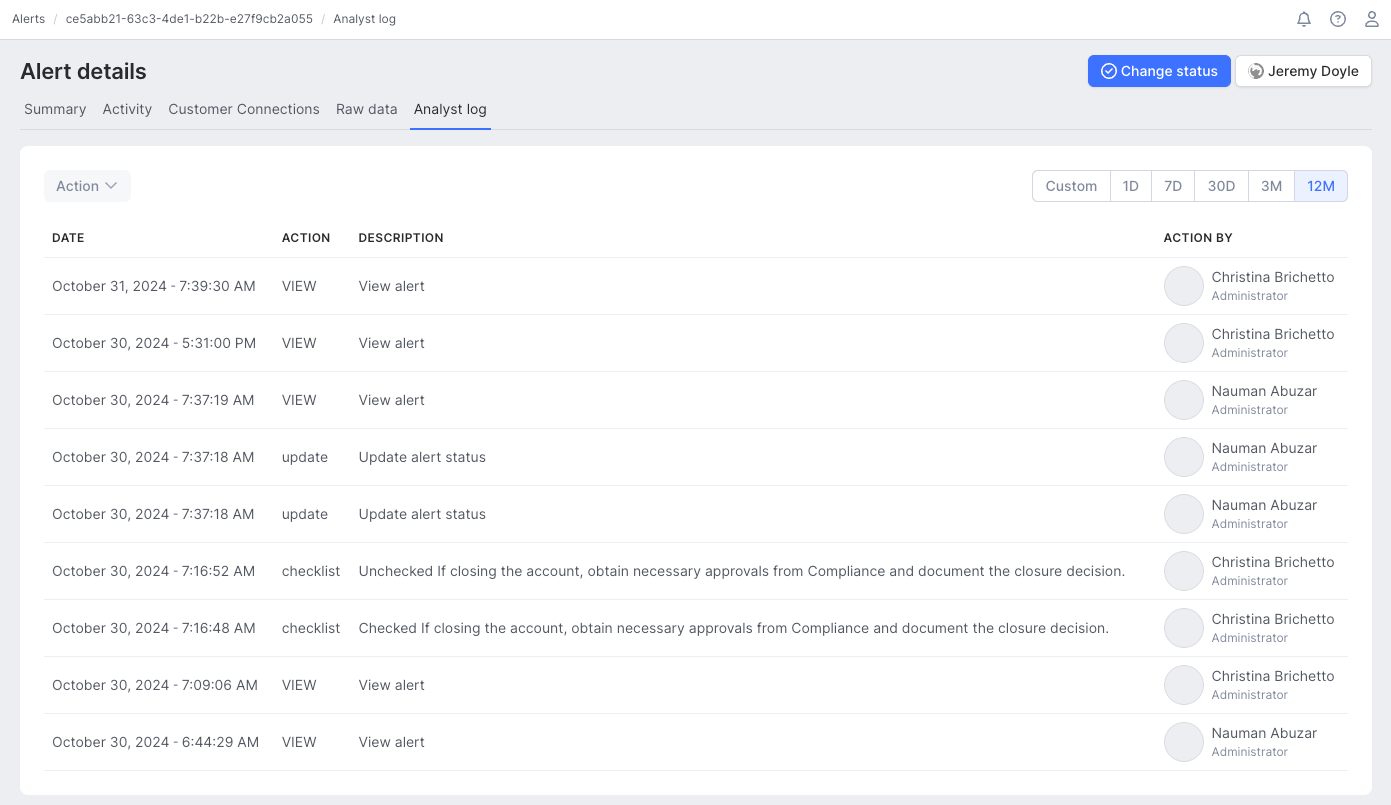
Maintain accountability with the Analyst log tab
The Analyst log tab tracks every action taken on the alert, ensuring complete transparency and accountability throughout the investigation process.
Within the Analyst log, you’ll find:
- Action history: A record of all updates, assignments and status changes related to the alert.
- Collaboration transparency: Track contributions from multiple analysts to ensure the full audit trail is captured.
From the Alert details page, you can:
- Assign or reassign the alert to a team member.
- Change the status of the alert as the investigation progresses.
By centralizing all relevant details, documents and logs, SEON empowers your team to handle alerts effectively, ensuring every investigation adheres to your internal policies and meets compliance standards.
Investigation checklists
SEON supports structured workflows by enabling customizable investigation checklists. These checklists ensure alerts are managed in accordance with your organization’s fraud and AML policies, reducing oversight and maintaining consistency.
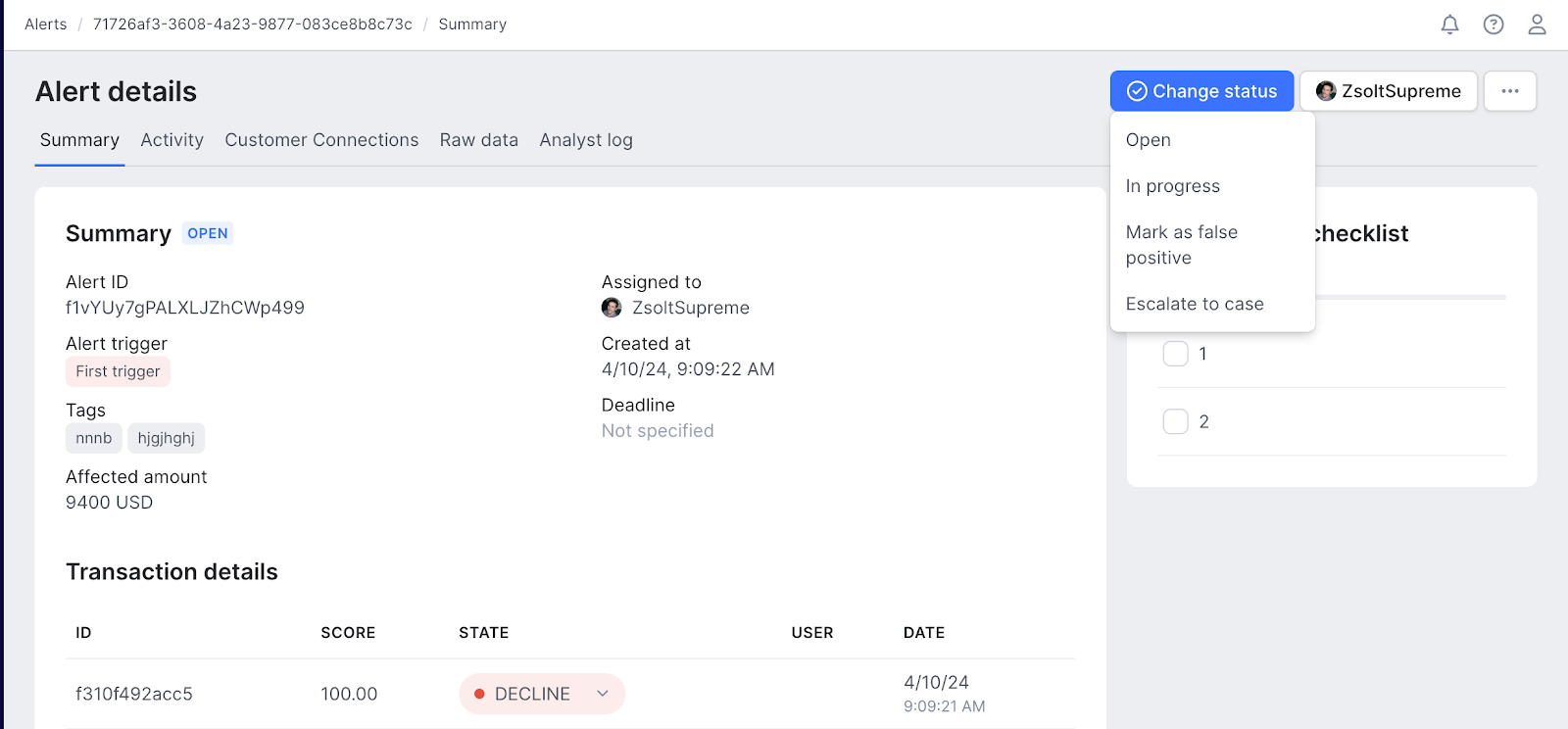
Alert statuses
All new alerts are initially created with an Open status, indicating that action is required. Once an analyst begins working on an alert, they should update its status to In progress to reflect ongoing activity.
Upon completing the investigation, the analyst has three options:
- Mark as false positive: For alerts determined not to be a threat.
- Close: For alerts where an issue was identified but no further action is necessary.
- Escalate to a case: For alerts requiring deeper investigation, escalating them creates a case entry in the Cases list.
Getting notified about alerts
Notifications ensure that you’re aware of critical events as they occur, allowing your team to respond promptly and effectively.